OT cybersecurity: 7 practices for patch & vulnerability management
Jan 2, 2024
With the increase of cyber attacks on operational technology (OT) systems in recent years, OT cybersecurity has become a top priority for organizations across industries. However, patching and securing OT environments—especially in large facilities with several devices from different vendors—presents unique challenges compared to IT cybersecurity.

What exactly do you need to know about patch management in OT? And how can you effectively manage vulnerabilities across your facility while juggling all your other tasks?
In this article, we’ll take a closer look at the challenges of OT patch and vulnerability management, and share best practices from OT cybersecurity experts Ari Rajamäki, Product Manager for Cybersecurity at Valmet, and Robert Valkama, Senior Manager, OT Cybersecurity at Fortum (photo above). Fortum is a Nordic energy company that carries out the operation and maintenance of power plants and offers energy-related services.
Why OT cybersecurity is so challenging—and important
Before delving into best practices, let’s consider why OT cybersecurity can often be neglected.
The gradual shift from analog to digital control systems over the last three decades has left many organizations overlooking the digital side of their operations. Unlike manual maintenance work, where processes are often well-documented and analyzed, businesses haven’t been giving the same attention to software updates and reconfigurations.
“Many businesses still only look at production or maintenance practices from the physical side without considering the digital aspects of their production environment. They haven’t adapted their operations because this digital transition happened so slowly over a long period of time,” explains Valkama.
Impending regulations like the new Network and Information Security Directive (NIS 2) and the Critical Entities Resilience Directive (CER) are driving the need for better cybersecurity across the EU and the globe.
And beyond compliance, ensuring OT cybersecurity is crucial for maintaining a safe and secure digital production environment. In 2021 alone, 80% of OT/ICS organizations reportedly experienced ransomware attacks. And OT cyber attacks can cause more damage than those in IT by causing harm to equipment, the environment, and human lives.
“If you’re running your plant with the help of digital systems, you won't ensure overall safety unless you take care of your OT security,” says Valkama.
Best practices for patch & vulnerability management in OT
Now, let's explore best practices to bolster your OT cybersecurity.
1. Take a holistic view of your site’s cybersecurity
The first step in managing OT cybersecurity is to adopt a holistic approach. It’s not just about updating software; there are alternative ways to control vulnerabilities.
“Even if a software patch would fix the problem, it might be quite expensive or impractical to do immediately. So consider other solutions as well. For example, can you mitigate the problem from a process perspective, or from a network perspective if it’s a network-based vulnerability?” says Valkama.
2. Do an OT asset inventory and prioritize critical devices
Before installing patches, conduct a thorough inventory of your OT assets. List all your vendors and devices, noting their age and functional expectations. “You need to know what you have to be able to develop,” summarizes Rajamäki.
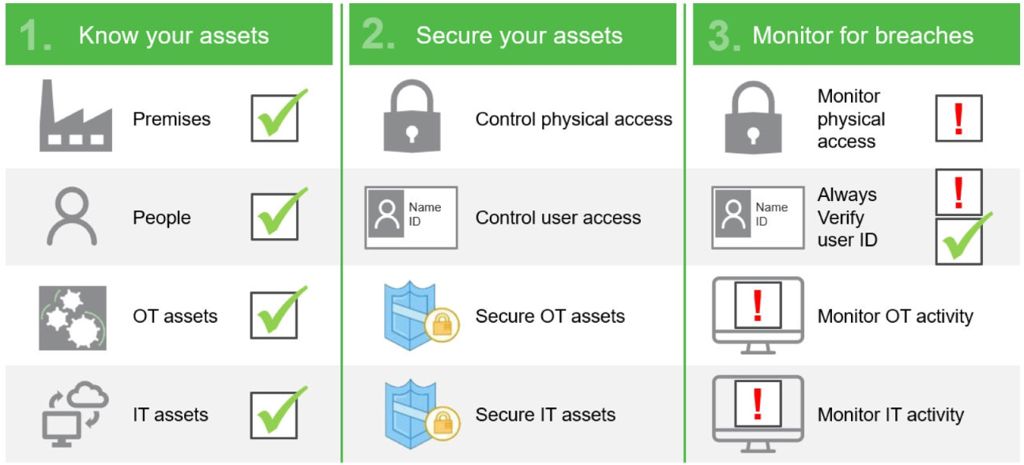
Identify your production's most critical devices and networks, and prioritize patching based on the risks they pose—whether it’s one machine or a computer network. Panic-patching everything simultaneously is counterproductive in OT. For a more effective cybersecurity strategy, focus on the process and address what truly matters.
“The biggest mistake you can make is to panic and try to do everything at the same time. Doing everything as soon as possible can be valid in IT, but it might not lead to the best results in OT,” says Valkama.
“We simply won’t be able to update everything and have the latest versions everywhere. So we need to be able to prioritize and look at what’s actually important,” he continues.
3. Create regular backups of your OT environment
Another step to take before patching is to ensure you have a reliable backup of your system, especially for critical components missing any patches or fixes.
“Many things can go sideways when you’re patching old components and you might need to roll back to the old version, which you’ll need to have available,” says Rajamäki.

4. Mitigate vulnerabilities with other protection capabilities
Since production downtime is usually required to install OT patches, you can’t reach the same patching frequency as with IT. Especially for facilities with 24/7 processes and tightly integrated systems—like power plants, paper mills, and water treatment plants—downtime is incredibly costly. You’ll need alternative protection measures to mitigate vulnerabilities during the time between updates.
Virtual patching is one technique that will give you time to evaluate patches and protect your vulnerable systems while you’re waiting to install updates. Whitelisting can also be a strong mitigation tool during waiting periods, blocking attacks by allowing only pre-authorized software.
5. Get help from your vendors
Instead of navigating the patching process alone, get support from your vendors. They can give you valuable insights into your system’s vulnerabilities, understand your patching needs, and help plan your upgrading roadmap.
Rajamäki highlights the importance of following vendor advice and preconditions to avoid breaking devices during patch installations. Vendors can also provide endpoint protection hardening, removing unnecessary features, functionalities, and users to minimize attack vectors.
As part of the patch and vulnerability management process, you need to follow up on the activity and effectiveness of your cybersecurity control. “This is the information and data you can expect from vendors: Where are we? How are we doing? Is this control only a paper tiger, or is it actually working?” says Valkama.
Vendors can also help with lifecycle management to avoid situations where you’re stuck with end-of-life products with no available patches.
“If you don't maintain the lifecycle of the products, you might end up in the situation where the original equipment manufacturer (OEM) vendor doesn't provide any patching, and your devices are left vulnerable,” says Rajamäki.
For example, while software providers like Microsoft regularly release software patches (on Patch Tuesdays), you won’t have access to any patches if you’re using a legacy system like Windows XP.
From a technical perspective, you cannot find anyone better than the vendor itself. But you still need somebody on your own team who understands the situation.
“Vendors like Valmet know the environment they’re handling. They can provide operators with a level of ease and confidence. From a technical perspective, you cannot find anyone better than the vendor itself. But you still need somebody on your own team who understands the situation,” says Valkama.
6. Cultivate in-house OT cybersecurity expertise
As an OT manager, you have to juggle many tasks. But cybersecurity can’t be neglected—make sure you have dedicated personnel who are continuously addressing it. That way, you’ll be able to foster the right mindset throughout the company and implement advice from vendors and governmental bodies.
To incorporate cybersecurity tasks into your routine, take the process slowly and focus on consistency. “Don’t only focus on cybersecurity once a year. Start building out the task list of what you should be doing and follow up on those every week or month. That way, you’ll learn quickly,” says Rajamäki.
7. Ensure your OT and IT teams talk to each other
Patch and vulnerability management requires a different approach in OT compared to IT, but it’s crucial for both teams to work together. Clear communication will bridge the gap, allowing teams to explain constraints, urgency, and decision-making processes.
“It’s really helpful to have clear communication between IT and OT. People can explain why they can’t do something, why they need to implement something fast, or why they’ve selected something to be used,” says Rajamäki.
Valkama also advises businesses to treat IT and OT cybersecurity equally on a reporting level to ensure a cohesive cybersecurity strategy.
Future-proof your OT assets
Managing OT cybersecurity requires a multifaceted approach and understanding of the unique challenges posed by industrial control systems. By adopting a holistic approach, implementing strategic patching, and getting support from your vendors, you can successfully safeguard your industrial operations in this digital era.
Text: Kelly Duval

